Invisible Wallet: Hiding Your Cryptocurrency Transactions
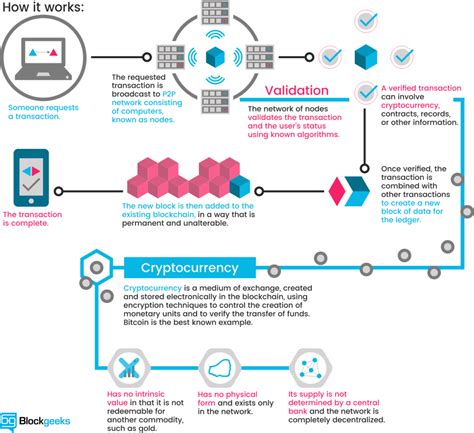
Cryptocurrencies have become increasingly popular in recent years, with the most recognized names being Bitcoin and Ethereum. However, unlike traditional investments, cryptocurrencies can be easily lost or stolen due to a lack of regulation and oversight by governments. As a result, individuals and businesses are now looking for ways to hide their cryptocurrency transactions from prying eyes.
What is an invisible wallet?
An invisible wallet refers to a digital storage system that uses advanced encryption techniques to protect your cryptocurrency assets. It is essentially a virtual vault that allows you to store, manage, and track your cryptocurrency assets without revealing them to others. With an invisible wallet, you can:
- Hide transaction history: By encrypting your transactions, you will be able to hide any suspicious activity or unauthorized access to your funds.
- Use pseudonyms: Invisible wallets often use pseudonymous addresses, making it difficult for others to track your cryptocurrency activities without permission.
- Anonymize Exchanges: You can use an invisible wallet to exchange cryptocurrencies anonymously, eliminating the need for intermediaries and reducing the risk of data leaks.
Popular Cryptocurrency Tools
Several tools are available that offer obfuscation features:
- Bitcoin Private
: A secure private key management system designed specifically for Bitcoin.
- Coinbase Wallet: A cryptocurrency exchange with a built-in invisible wallet feature, allowing users to store and manage their coins without revealing themselves to others.
- Ledger Live: A decentralized digital storage service that offers encryption and pseudonymization of user data.
- Crypter: A platform that allows you to create custom invisible wallets for specific cryptocurrencies.
How to Use an Invisible Wallet
To get started with an invisible wallet, follow these steps:
- Select a Cryptocurrency
: Choose the one you want to hide your transactions for and install the appropriate software or hardware.
- Generate Private Keys: Create new private keys for your coins using specialized tools or services.
- Store and Manage Funds: Transfer your crypto to your invisible wallet, just like normal transactions, but keep in mind that all data is encrypted.
Security Considerations
While an invisible wallet can provide a high level of security, it is still important to take additional precautions:
- Use strong passwords: Create complex passwords for your account and be wary of using weak or easily guessable passwords.
- Keep your software up to date: Regularly update your operating system, wallets, and encryption software to ensure that the latest security patches are installed.
Conclusion
Hiding your cryptocurrency transactions with an invisible wallet is a valuable tool that can help protect your assets from unwanted access. By using specialized tools and services, you can enjoy enhanced anonymity and security while enjoying the benefits of the cryptocurrency revolution. However, remember to always take extra precautions when managing your digital assets.
Please note: This article provides general information on the topic of concealing cryptocurrency transactions with an invisible wallet. It is essential to consult a financial advisor or expert in the field before making any investment decisions or implementing new services.

