The Ethereum Finney Attack: Understanding Its Purpose, Prerequisites, and Methods
Ethereum, one of the leading blockchain platforms, has been vulnerable to a type of exploit known as the “Finney Attack.” This malicious technique allows attackers to manipulate the Ethereum network’s transaction history, potentially disrupting the security and integrity of the network.
What is a finney attack?
The decentrals the decentralized nature of blockchain transactions. The Ethereum Network. The attacks then broadcasts these fake transactions, which are essentially duplicates of the original one.
The primary purpose of a finney attempt is to manipulate the network’s translation history and create inconsistencies in the blockchain. This can lead to various problems, including:
*
.
Prerequisites for a Finney Attack
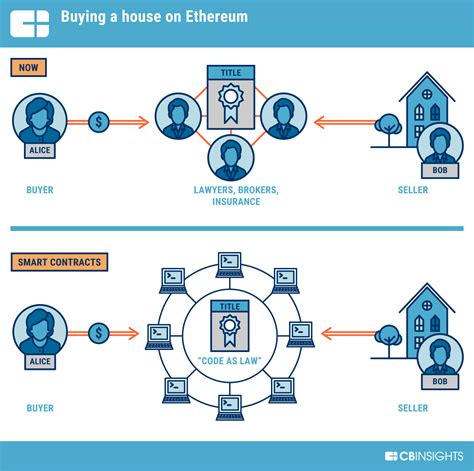
To carry out a finney attempt, an attacker must have two things:
- **
- Access to multiple accounts with sufficient funds :
How does a Finney Attack Work?
Here’s a step-by-step explanation of the process:
1.
2.
*
Origin of the Name “Finney Attack”
Charles C. F. Finney, a British Banker and Financier who was instrumental in developing the first public stock exchange in London. In 1872, Finney’s firm processed millions of dollars’ worth of transactions daily, making him one of the most skilled traders of his time.
The term “finney attempt”

